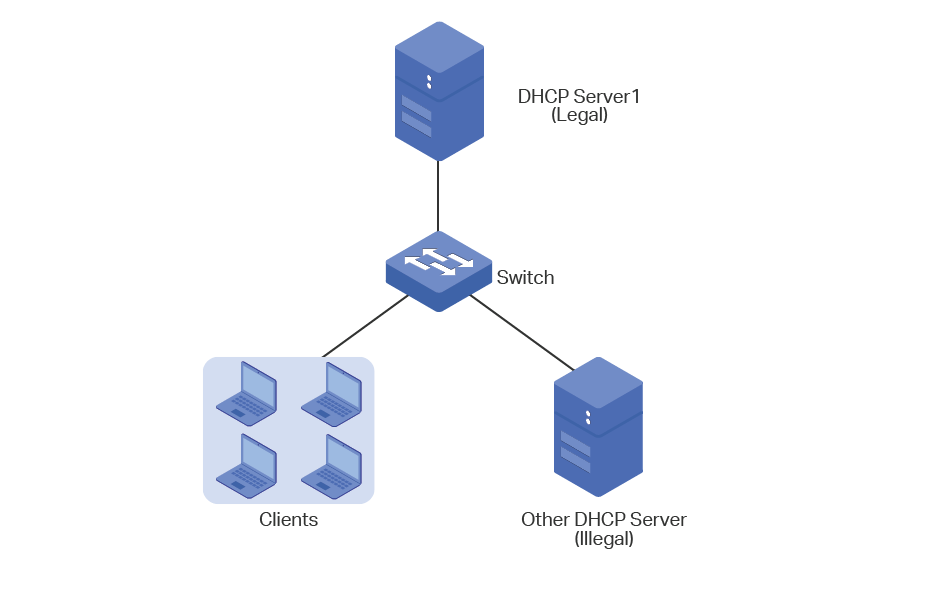
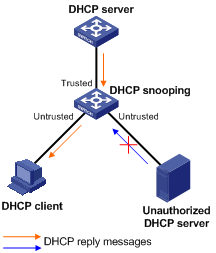
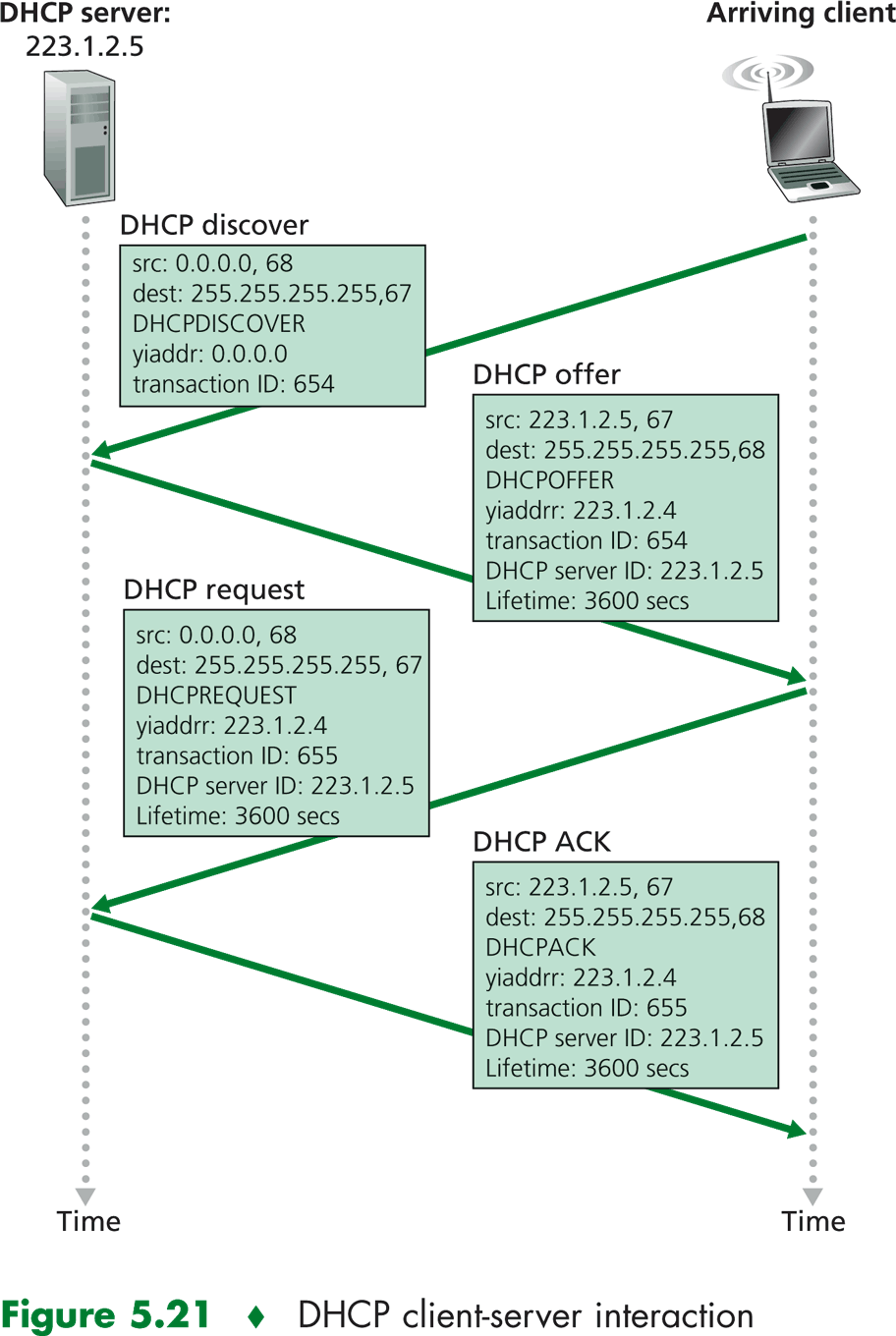
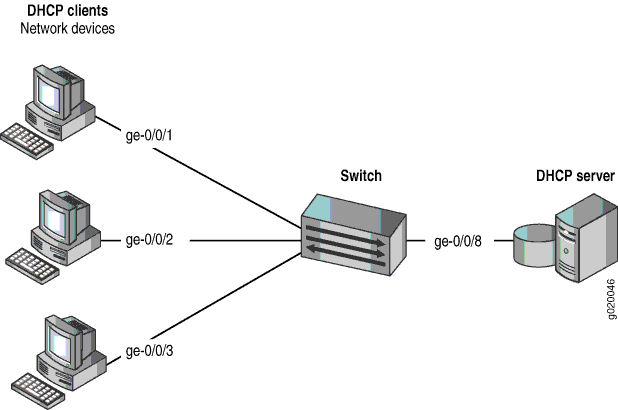
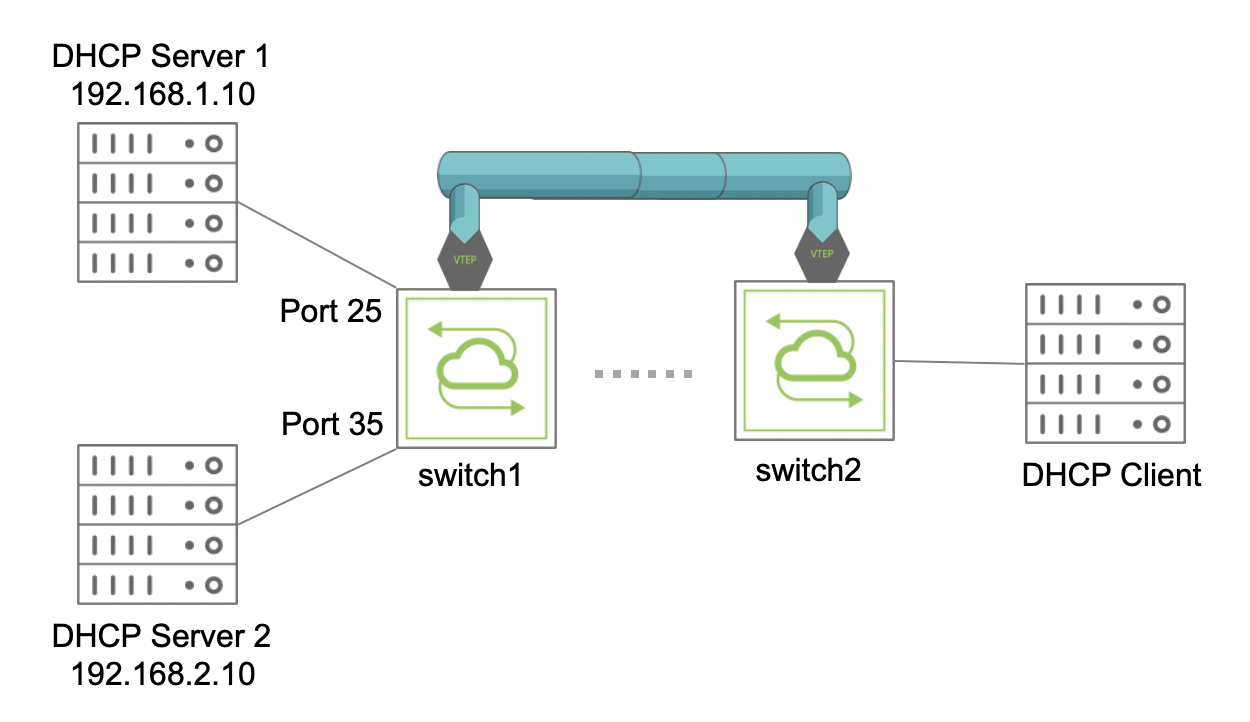
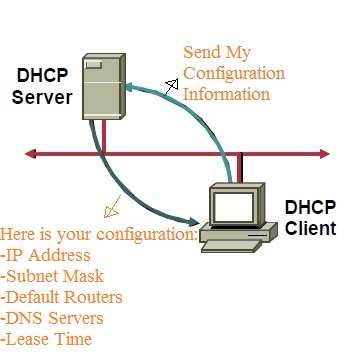
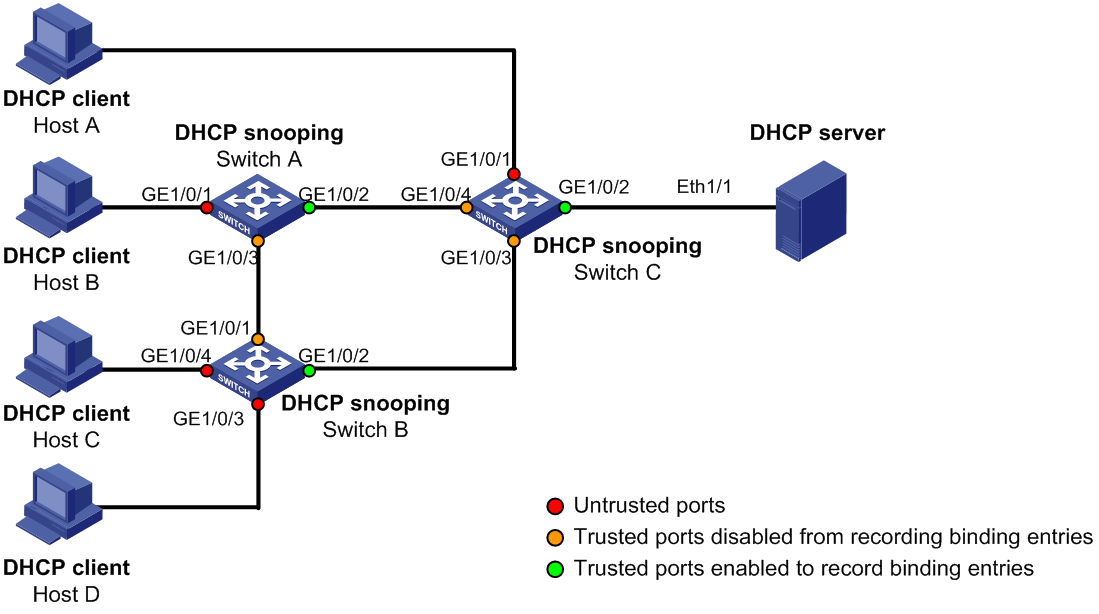
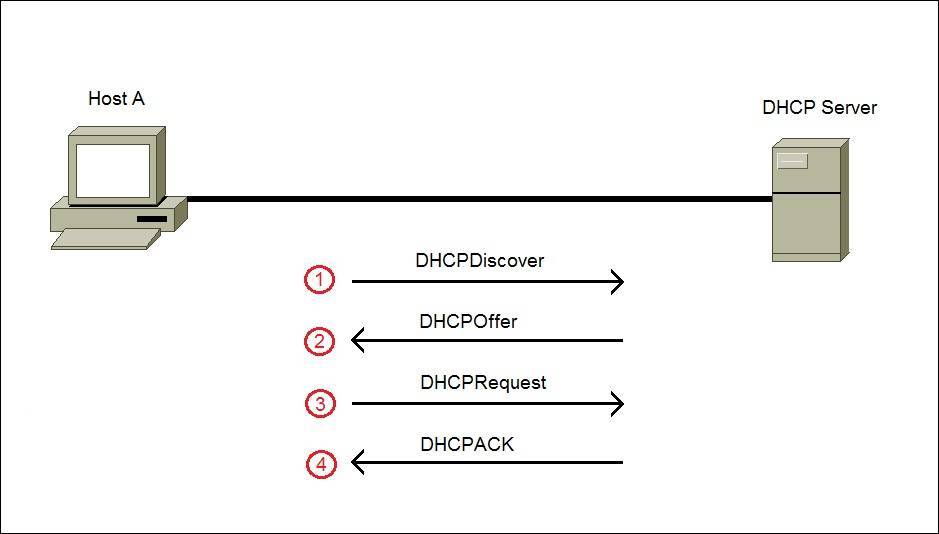
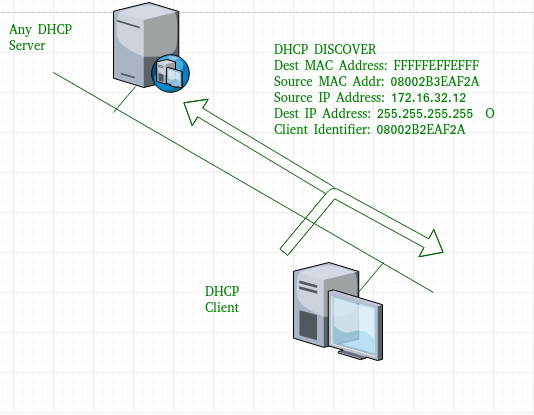
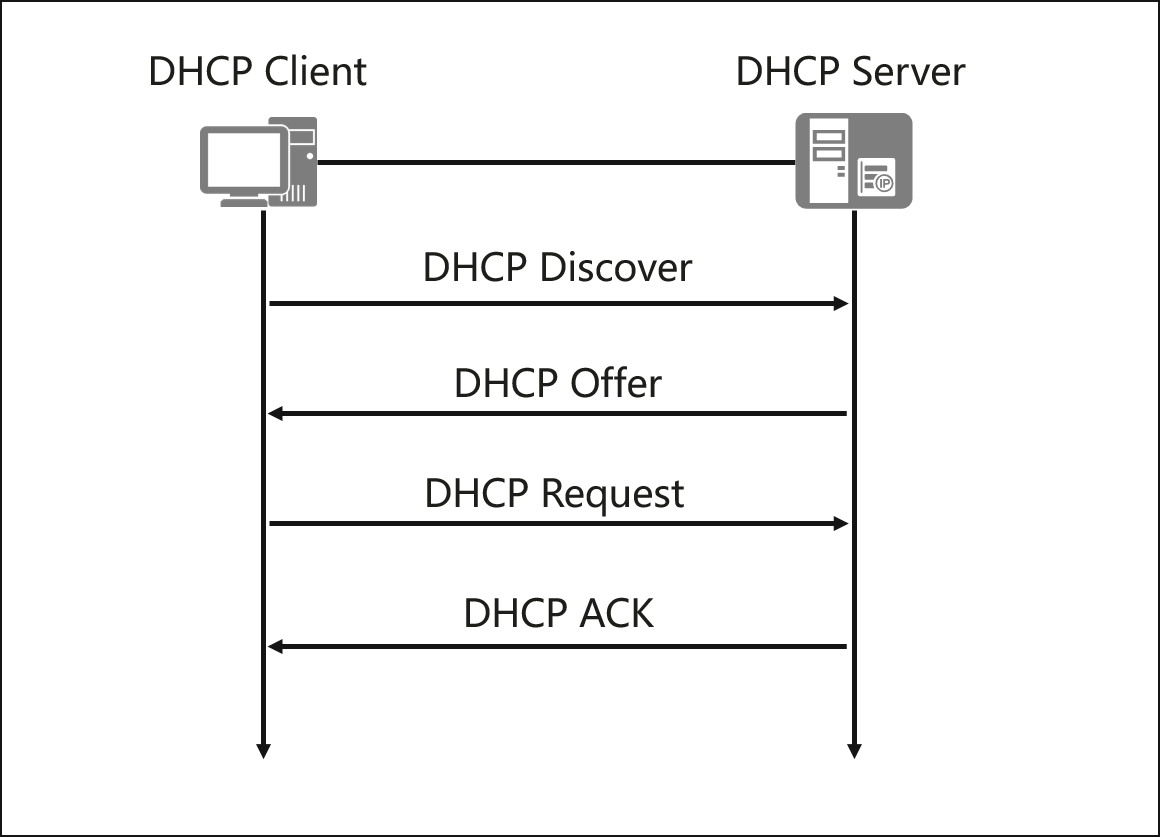
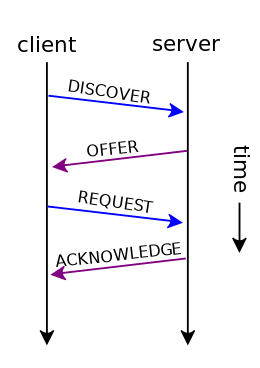
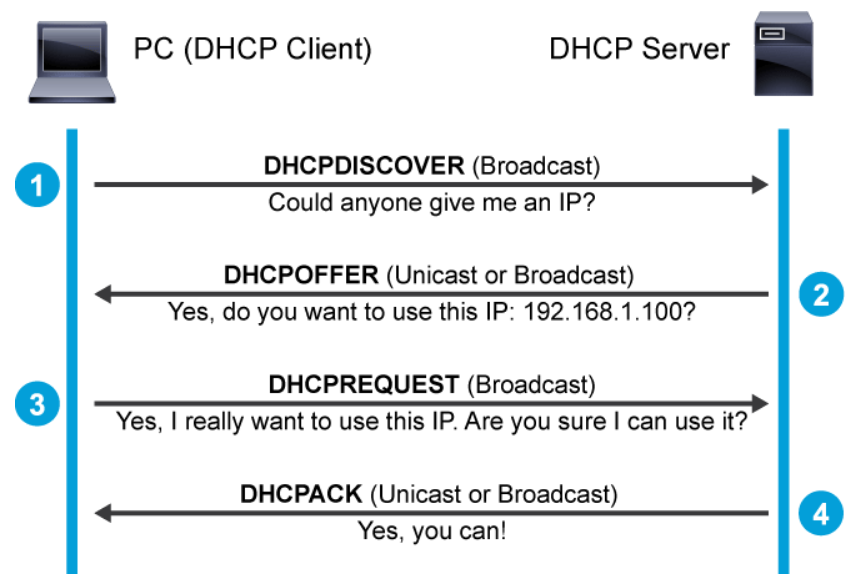
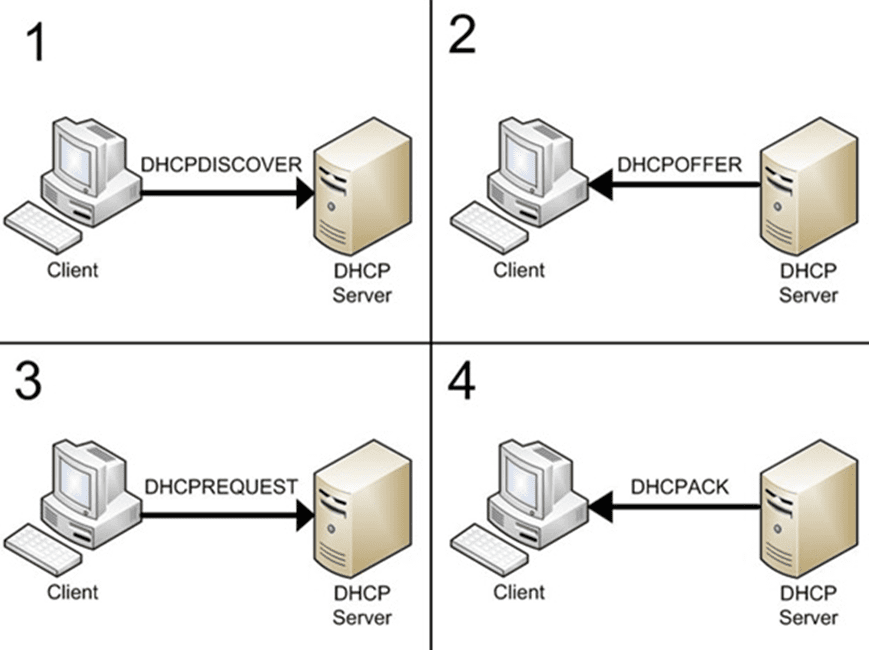
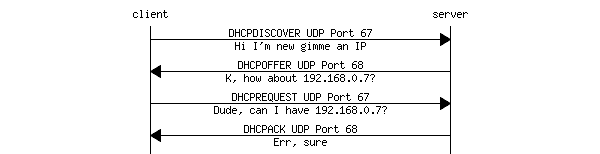
Understanding DHCP Snooping and Basic Configurations : Cisco, Juniper and Huawei - Route XP Private Network Services
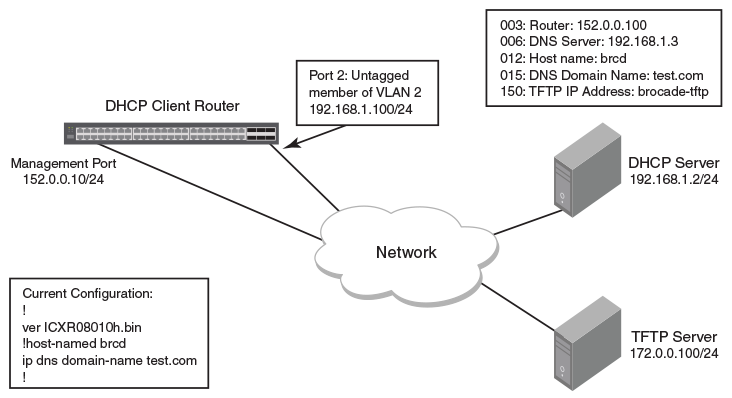
Interaction Scenario for Port Mapping and DNS Location Updates Besides... | Download Scientific Diagram
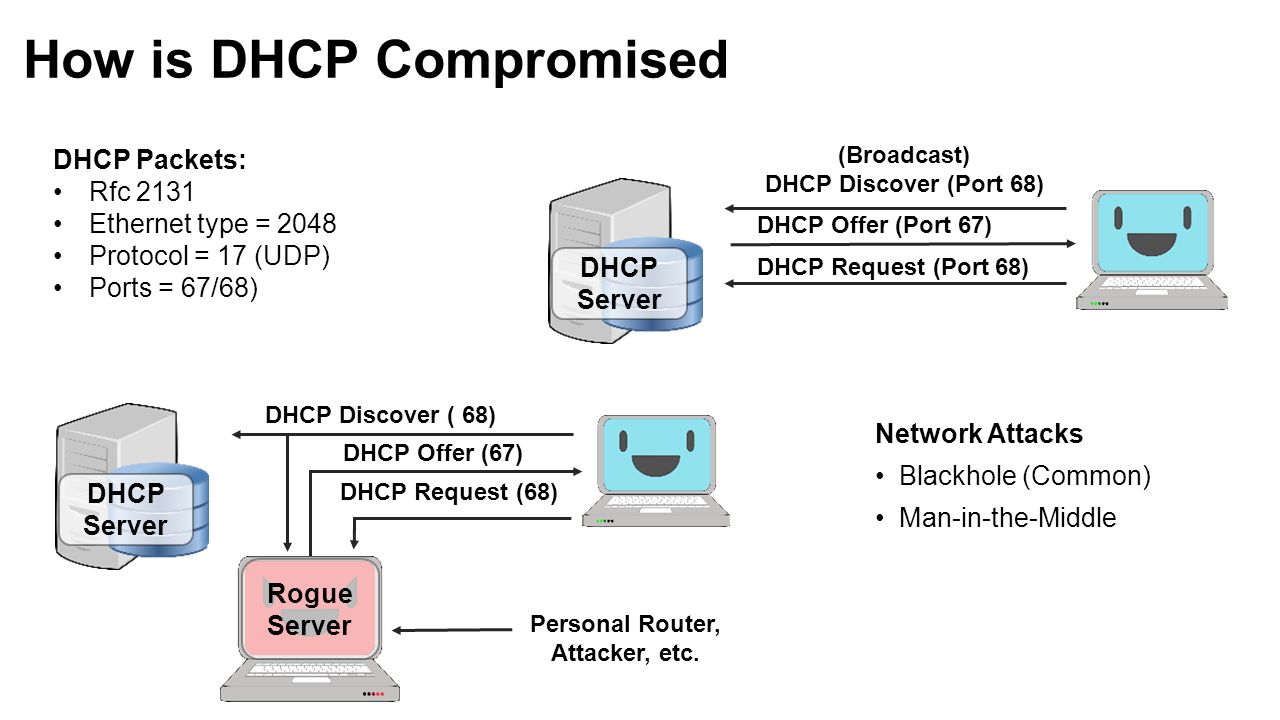
Leveraging SDN to Improve the Security of DHCP Presented By Jacob H. Cox Jr. For SDN NFV Security Workshop 2016 On 10 March ppt download